Attacking Shimano Di2
Last year, security researchers found vulnerabilities in popular bicycle parts that allow an attacker to shift someone else's bike or make it impossible for the rider to shift themselves (source). The bike I recently bought has Shimano Di2 components and is vulnerable to this attack if it runs outdated firmware.
This blog post is about reproducing the replay attack. The attacker needs a software-defined radio (SDR) and must be within a couple of meters of the bike. For a recreational rider, it is incredibly unlikely to be targeted, and even if it were the case, it would probably have few consequences. For a professional rider, the odds are very different. Shimano published a secure firmware, so if your bike is up to date, you are safe. For many of the components, you can also connect the shift levers to the battery, which makes this attack impossible even on outdated firmware, and your battery will last approximately 50% longer. The previous post was about downgrading the firmware of my shift levers and rear derailleurs in order to get them into a vulnerable state. For more information, you can read the detailed post about the downgrading.
Replay Attack
The attack is very simple. The shift levers communicate with the rear derailleurs wirelessly. This signal can be received by an attacker who has a software-defined radio (SDR) and is nearby. The bike has no replay protection in firmwares 4.2.1 and lower. All that is needed for the attacker is to record the signal that the shift levers send to the rear derailleur. They can then transmit the recorded signal whenever they want to shift the bike.
The authors of the paper mention using the program Universal Radio Hacker for their attacks. They also report a signal frequency of 2.478 GHz with a bandwidth of 2 127 kHz. I used the same program with the same parameters to record the signal. The SDR I used is a HackRF One. I pressed the shift levers multiple times to shift up and down. The moments are clearly distinguishable in the recorded trace. There are vertical lines in the trace that repeat after the same duration. When pressing the lever, there are multiple shorter vertical lines close to each other.
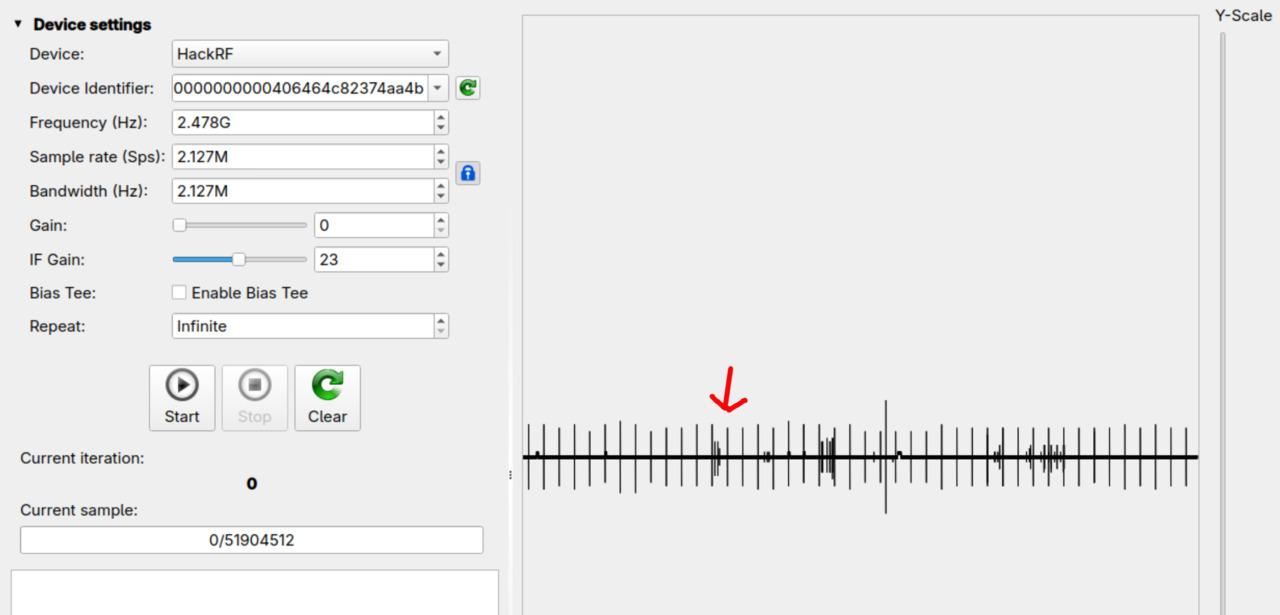
I then used the same program to transmit the recorded signals. When replaying the signal, only the first shift worked for me. I didn't have time to investigate why the others did not work, but it might be that the signal was too noisy or too weak. Replaying the same signal again had no effect until I pressed the shift lever. The authors mention that the signal contains multiple packets and one of them notifies the bike of the release of the shift lever. Since only the first recorded signal worked for me, it could indicate that there was some issue with my recording and that the release notification was damaged. This would explain my observation.
Demonstration and Conclusion
The attack partially worked. You can see a video of it below. In it, you can see the bike in a stand and a HackRF One (SDR) connected to a laptop. On the screen, you can see Universal Radio Hacker replaying the recorded signal. The signal that works are the first small vertical lines. Once the blue bar reaches that spot, the rear derailleur moves and the gear is shifted. In the video, you can see that the shift levers are never pressed.
It was a lot of fun to reproduce the attack and play around with an SDR and my bike. If I had more time, I would try demodulating the signal to see what actually gets sent and compare it with the authors’ findings. This could also improve the quality of the replayed signal. It would also be interesting to record a signal with updated firmware and compare it to see if the fix was sufficient. Alternatively, the firmware files could be analyzed.
Please let me know if you have any comments about this post, ideas, or further insights into the Di2 components and their vulnerabilities.